US Cyberspace Implementation Stalling
US CSC report states the ability to protect itself and allies from cyber threats is stalling
Apparently the US is slipping behind peer nation states with respect to cyber operations, strategy and implementation of core structural change.
The recent U.S. Cyberspace Solarium Commission’s (CSC’s) annual report on implementation started its report with a scathing introduction:
“Our nation’s ability to protect itself and its allies from cyber threats is stalling and, in several areas, slipping. For five years, the U.S. Cyberspace Solarium Commission’s (CSC’s) recommendations have served as a benchmark against which to measure policymakers’ commitment to strengthening the nation’s cybersecurity. This report assesses that approximately 35 percent of the commission’s original 82 recommendations have been fully implemented, 34 percent are nearing implementation, and an additional 17 percent are on track to be implemented. By comparison, however, last year’s report concluded that 48 percent had been implemented, 32 percent were nearing implementation, and an additional 12 percent were on track. For the first time, there has been a substantial reversal of the advances made in previous years. Nearly a quarter of fully implemented recommendations have lost that status — an unprecedented setback that underscores the fragility of progress.”
That is a pretty damning verdict. Of course in recent months federal budgets across a host of US services have been cut and it seems cyber is also part of that. Reports like this of course do no harm in amplifying the need for more personnel and resources.
Zooming, out what is the both the report and US cyber capabilities in general trying to achieve?
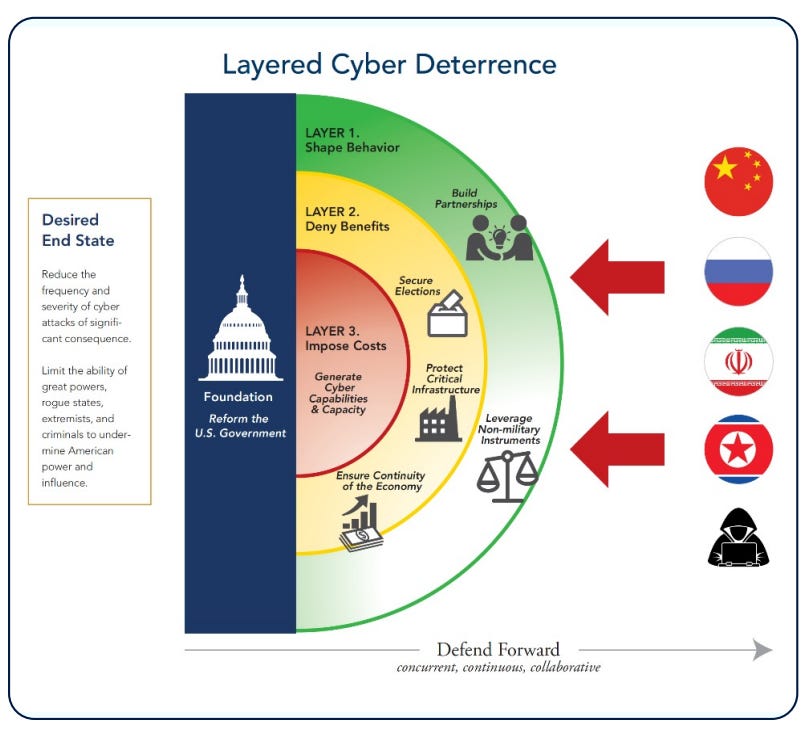
Image Source: CSC Report
The ability to deliver “layered cyber deterrence” is a powerful objective - which basically aims to reduce the frequency and severity of cyber attacks. Both of those points (the likelihood and impact in standard risk management parlance) are complex things to both achieve and measure.
Hardening defences is one aspect, but identifying and in turn attributing attacks to actors linked to nation state orders is also another. The ability to consistently call out attacks, attribute specifically and support with technical evidence (often in line with a broad cast of allies, academia, technology providers and legal stakeholders) is becoming a powerful deterrence in itself. Actor and sponsor denials can only go so far.
The report goes in detail to specify where the US with respect to its strategic cyber progress.
Overall Assessment
Only 35% of the CSC’s 116 recommendations have been fully implemented (down from 48% in 2024).
34% are nearing completion, 17% on track, and the rest face limited progress or major barriers.
Nearly one-quarter of previously implemented reforms lost their status, showing fragility in institutional progress.
Leadership gaps, budget cuts, and administrative turnover have slowed coordination, especially at CISA, the State Department, and the Office of the National Cyber Director (ONCD).
Strategic Framework: “Layered Cyber Deterrence”
The CSC’s cyber strategy centers on three layers of deterrence:
Shaping behavior — promoting norms of responsible state behavior through diplomacy.
Denying benefits — hardening critical infrastructure and aligning public-private cyber defenses.
Imposing costs — disrupting adversaries through law enforcement and military operations.
The report finds that:
The U.S. continues to apply this model inconsistently.
Technical progress is outpacing federal reform.
Cyber diplomacy, talent development, and collaboration are under-resourced.
Top Five Recommendations for 2025–26
Enhance ONCD’s Authority
Give ONCD budgetary and regulatory coordination powers to align cyber policy across agencies.
Trump should issue an executive order revising Presidential Policy Directive 41 to grant ONCD formal convening power.
Restore CISA’s Workforce and Funding
CISA faces a 17% budget cut and up to one-third workforce loss.
Congress should provide multiyear stable funding to maintain its role as the national coordinator for critical infrastructure resilience.
Rebuild Cyber Diplomacy at the State Department
The Bureau of Cyberspace and Digital Policy (CDP) lost key staff and funding, impairing U.S. engagement abroad.
The report urges restoration of CDP’s capacity to counter PRC digital influence and support allies.
Reinstate Public–Private Collaboration Mechanisms
The administration’s termination of CIPAC (the Critical Infrastructure Partnership Advisory Council) has eroded industry trust and chilled information sharing.
Congress should restore legal protections for private-sector collaboration.
Expand and Diversify the Cyber Workforce
Workforce cuts and the rollback of diversity programs have shrunk the talent pipeline.
The U.S. should reinvest in skills-based hiring, apprenticeships, and retention incentives.
Key Takeaways
Cyber deterrence is faltering — adversaries like China continue large-scale intrusions despite U.S. actions.
Institutional reforms remain fragile without sustained funding, legal authority, and bipartisan political will.
The U.S. needs to restore trust with industry and allies, reinforce its cyber diplomacy capacity, and rebuild a resilient domestic cyber workforce.
In essence, the CSC report warns that the U.S. cyber strategy risks erosion without renewed executive and congressional action to institutionalize past progress and adapt to accelerating threats.