North Korean Linked Lazarus Expands Attacks to European Drone Makers
A recent research article by ESET (available here) highlights the evolution of the Lazarus group to now attacking UAV (unmanned aerial vehicles or drones) manufacturers and suppliers across Europe. They claim is part of a strategic initiative by North Korea to bolster its own drone operations.
They state:
“ESET researchers have recently observed a new instance of Operation DreamJob – a campaign that we track under the umbrella of North Korea-aligned Lazarus – in which several European companies active in the defense industry were targeted. Some of these are heavily involved in the unmanned aerial vehicle (UAV) sector, suggesting that the operation may be linked to North Korea’s current efforts to scale up its drone program. This blogpost discusses the broader geopolitical implications of the campaign, and provides a high-level overview of the toolset used by the attackers.”
It sounds like a potential two-bird win for Lazarus - in the sense of helping to disrupt existing manufacturers of potentially enemy operators (aka Ukraine and those supporting Ukraine against Russia, which North Korea is an ally) as well as helping streamline and optimize their own drone and UAV systems designs through mere intellectual property theft.
Strategic purpose
The attacks likely sought intellectual property and manufacturing know-how to accelerate North Korea’s drone program, which is expanding with Russian assistance and modeled on U.S. systems such as the RQ-4 Global Hawk and MQ-9 Reaper.
Victims made parts for UAVs currently deployed in Ukraine, suggesting Lazarus wanted data on Western-made weapons used on the front line.
The campaign aligns with Pyongyang’s pattern of reverse-engineering foreign UAV designs via cyberespionage.
Image Source: ESET report on new Lazarus attack patterns
Attack chain and tools
Initial access: classic DreamJob social-engineering — fake “dream job” offers sent to defense engineers with a malicious PDF reader that installs malware.
Loader stage: trojanized open-source projects from GitHub (e.g., TightVNC Viewer, MuPDF Reader, DirectX Wrappers, Notepad++ plugins).
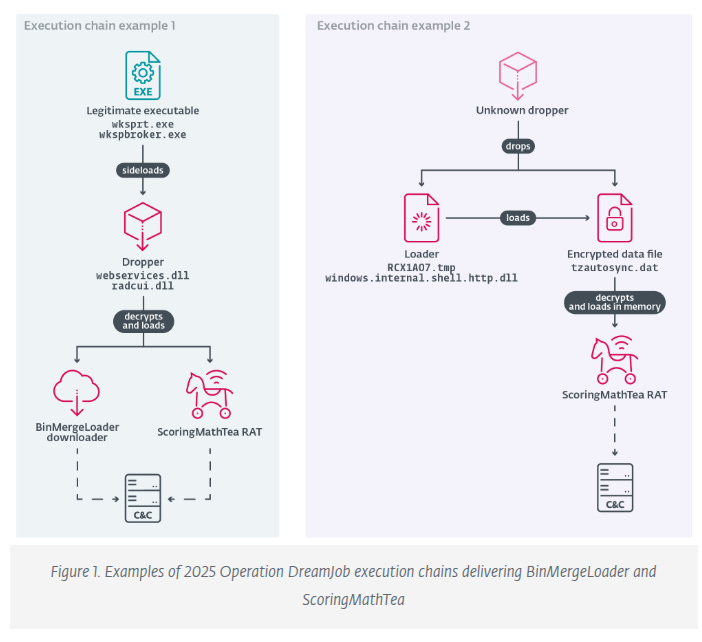
DLL proxying/side-loading: fake system libraries such as
DroneEXEHijackingLoader.dll,webservices.dll, andradcui.dllrun under legitimate Windows executables.Main payload: ScoringMathTea, a 40-command remote-access trojan giving full control of the host, using encrypted HTTP/S C2 via compromised WordPress servers.
Encryption and reflective DLL injection keep payloads only in memory; data are exfiltrated through the C2 channel.
Take Aways
ESET attributes the campaign to Lazarus with high confidence. The “DroneEXE” internal naming, target selection, and timing indicate an espionage operation in support of Pyongyang’s UAV industrial expansion.
In essence, North Korea is combining social-engineering intrusion with code theft to steal UAV blueprints and production methods, improving its own drone arsenal and export capability.